VENDILIGENCE™
System and Organization Controls (SOC) Assessment
Our SOC Assessment provides an in-depth analysis of your vendor's SOC reports, assisting you in ensuring their control environment is secure and compliant. This assessment allows you to easily understand your vendor's controls, helping protect your sensitive data and maintain regulatory compliance.

PRODUCT TOUR
See it in Action: Take a tour of the System and Organization Controls (SOC) Assessment
By delegating the complex task of SOC review to us, your team can receive a thorough look at your vendor's control environment. Our assessment identifies key controls and gaps, supporting your efforts to meet necessary standards and assisting you in making informed decisions with confidence.
Most Commonly Used For:
Financial Services Firms, Cloud Service Providers, and Healthcare Vendors
Our streamlined process thoroughly analyzes your vendor's SOC report, providing clear insights into their control effectiveness and compliance.
-
Expert Analysis
-
Regulatory Compliance Assurance
-
Comprehensive Control Coverage
-
Focused and Efficient

Expert Analysis
Our team of information security professionals, including CTPRPs, CISMs, CISAs, CISSPs, ABCPs, and more, meticulously reviews your vendor's SOC reports. They evaluate the effectiveness of controls, identify gaps, and provide actionable insights in a focused and readable format.
Regulatory Compliance Assurance
Our assessment helps you ensure that your vendor's controls meet industry standards and regulatory expectations. This aids in maintaining compliance and avoiding regulatory issues, with clear gap and exception callouts for quick identification and resolution of potential issues.
Comprehensive Control Coverage
We provide a thorough outline of all key points and recommendations within the SOC Assessment. This ensures auditors and examiners have a clear and complete understanding of critical elements, streamlining their review process.
Focused and Efficient
Our SOC Assessment is designed to concentrate on essential information, making it straightforward and user-friendly. This approach facilitates a more effective evaluation process for your examiners or auditors.
In our SOC Assessment, we include Report Comments and Recommendations to help you request further details or clarifications from your vendors as needed. This feature supports effective communication, ensuring you can address and resolve issues promptly.
Risk Areas Assessed

Subservice Organizations
We review the reliance on external entities for service delivery by the vendor, highlighting their use and helping to easily discover potential areas of increased risk arising from this third-party service.
Organization and Administration
We review the involvement of senior management in IT security, employee adherence to policies, thoroughness of background checks, and effectiveness of vendor management practices, providing insights into the administrative controls and their enforcement.
Information Systems
We look to validate that comprehensive security measures including, IDS/IPS, antimalware defenses, web application firewalls, and encryption practices, are in place. We also review change, incident, and patch management procedures, assisting you in ensuring robust information system security.
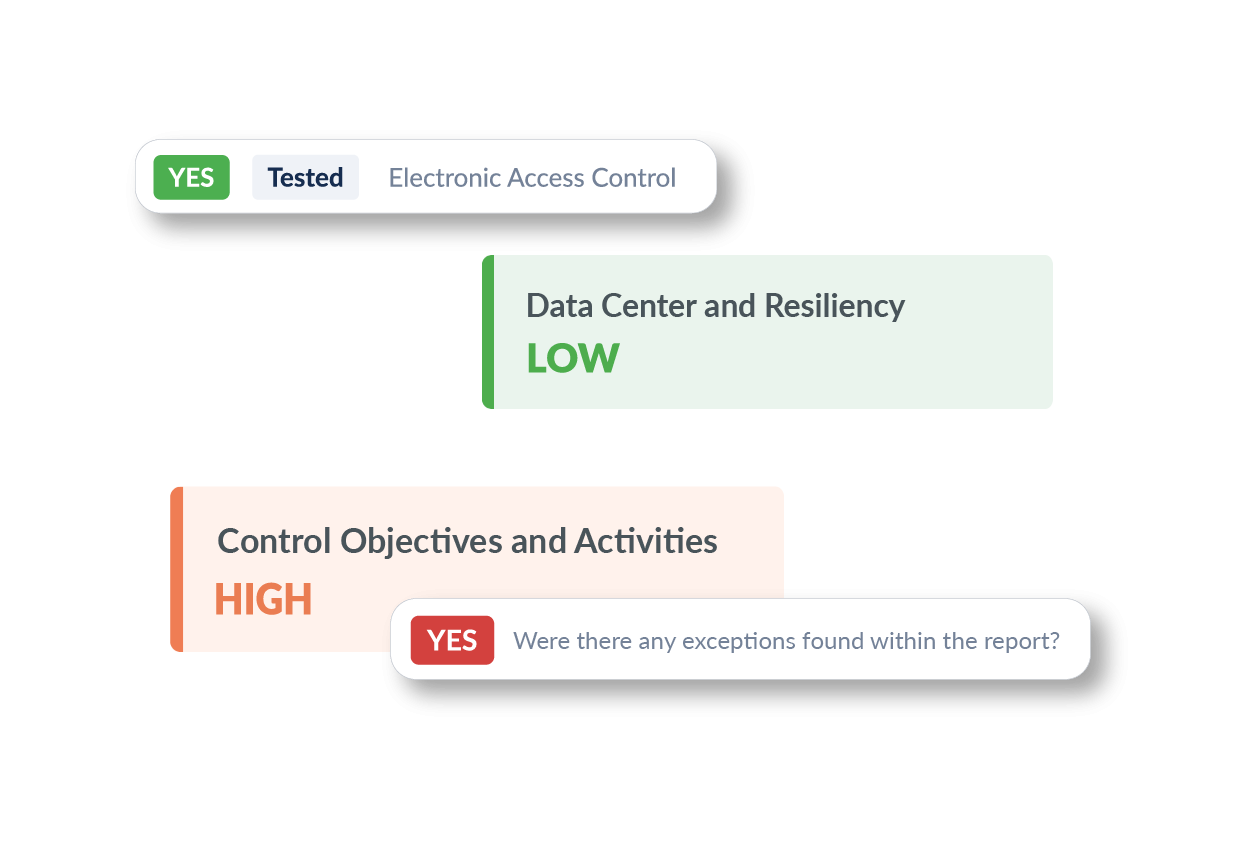
Data Center and Resiliency
We assess physical security measures and environmental controls such as electronic access, security personnel, cooling systems, and fire suppression, as well as the robustness of backup procedures to maintain data integrity and operational uptime.
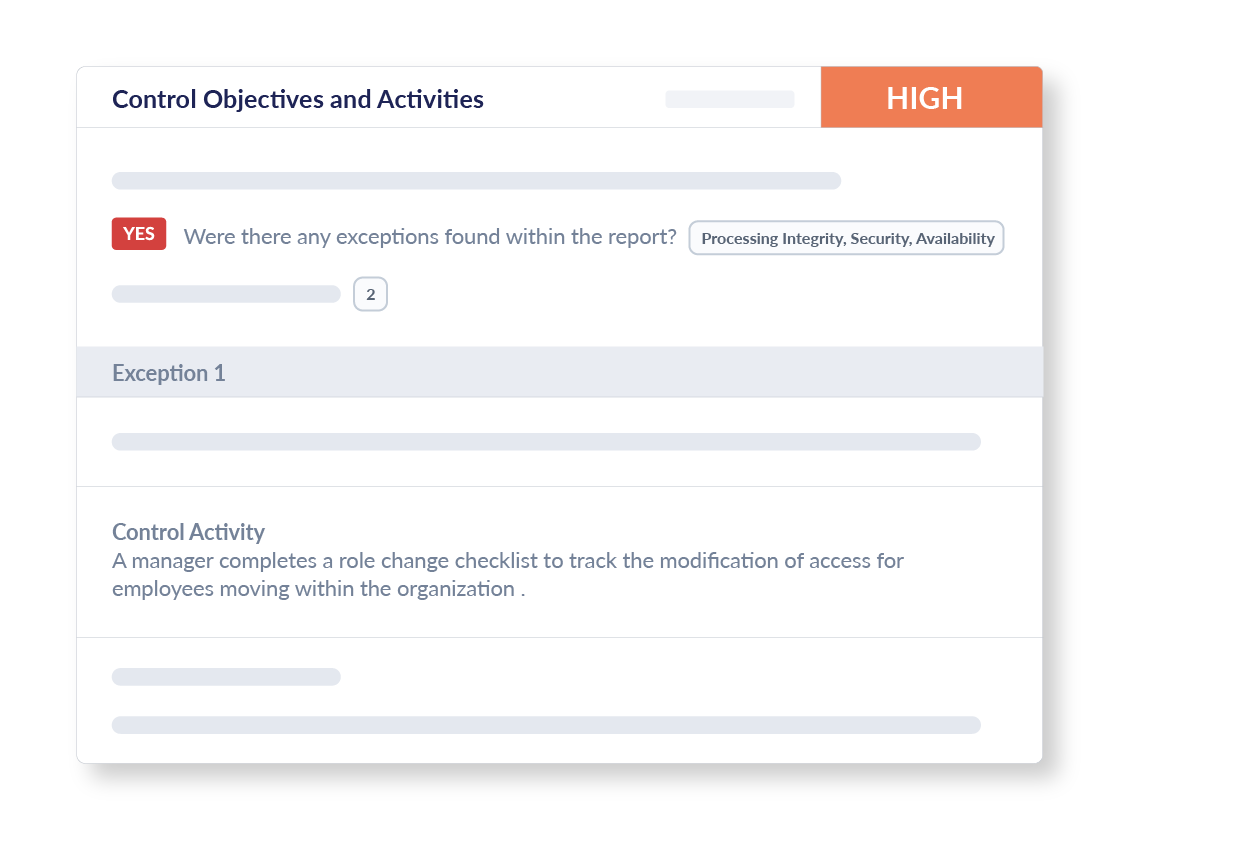
Control Objectives and Activities
Our assessment helps you focus on the effectiveness of specific control activities by reviewing exceptions found in SOC reports and assessing overall impact and providing a detailed and easy to digest summary of any issues found.


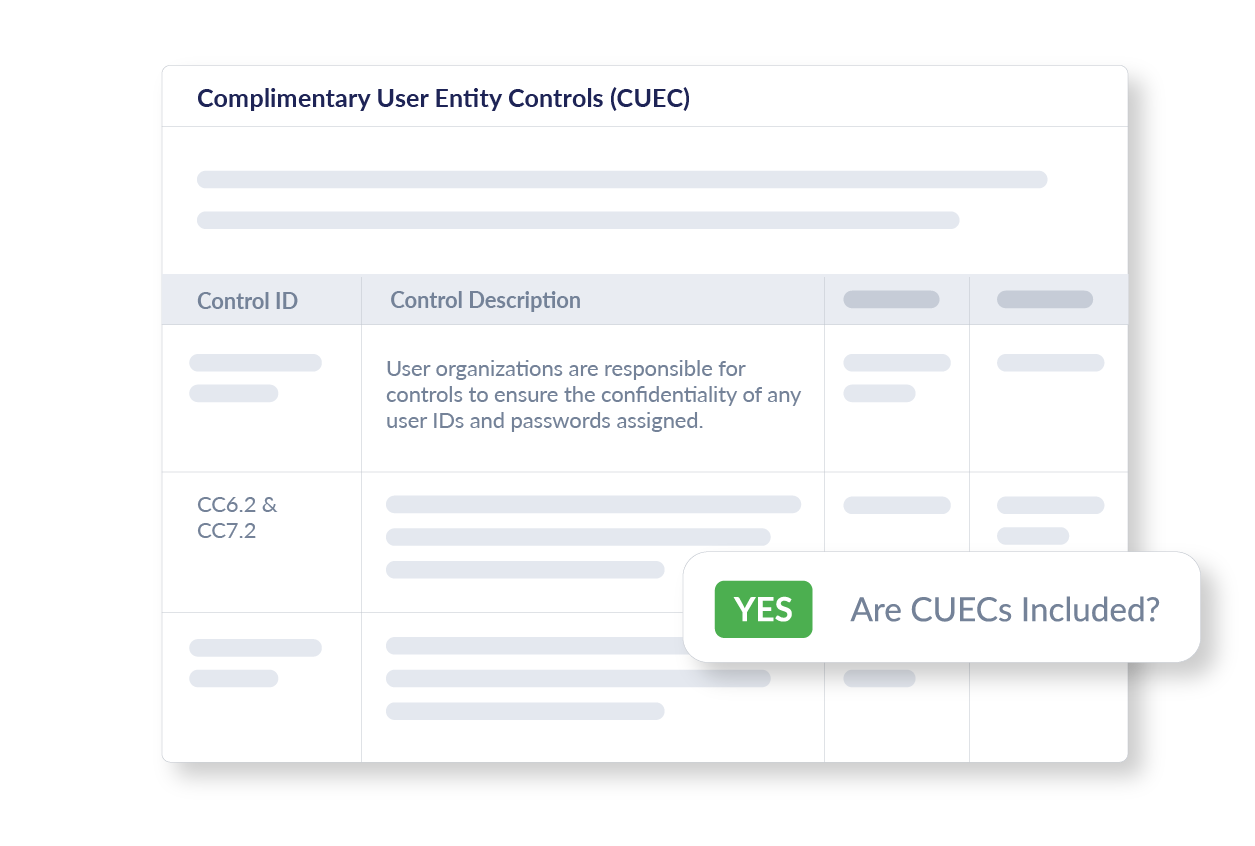
Complementary User Entity Controls (CUECs)
This section details organizational responsibilities in maintaining controls that complement those of the vendor, helping to foster a comprehensive security strategy that covers all aspects of user and vendor responsibilities.
How it works
STEP 1
Gather Essential Information
We start by collecting foundational details about each potential vendor, such as corporate address, key contacts, and a brief description of their services. This helps us understand the vendor's business identity and operational scope.
STEP 2
Analyze SOC Report
Our team conducts a detailed review of your vendor's SOC report, focusing on key areas such as subservice organizations, organization and administration, information systems, data center and resiliency, control objectives and activities, and complementary user entity controls (CUECs).

STEP 3
Consolidate and Review Findings
Collected data and assessment results are consolidated to provide a clear picture of the vendor’s control environment. This overview allows for an initial assessment of the vendor's reliability and compliance.
STEP 4
Facilitate Informed Decision-Making
You receive a comprehensive document detailing the findings from the SOC assessment, available directly on the Venminder platform, and is downloadable to easily share offline. This information aids your organization’s leaders in making informed decisions.

Discover why Venminder
is top-rated by customers
Know if vendors and suppliers are in compliance with
industry guidelines, frameworks, standards and laws
Technology Standards and Frameworks
NIST 800-53 Rev. 5
ISO/IEC 27001:2022
NIST Framework for Improving Critical Infrastructure Cybersecurity version 1.1
AICPA Trust Services Criteria
Center for Internet Security - Critical Security Controls
Regulations, Statutes, and Laws
EU General Data Protection Regulation
New York Department of Financial Services 23 NYCRR 500
Health Insurance Portability and Accountability Act
Interagency Guidelines Establishing Information Security Standards
Directive (EU) 2022/2555 on Measures for a High Common Level of Cybersecurity Across the Union
New York Department of Financial Services - 23 NYCRR 500
Industry Guidance
FFIEC IT Examination Handbook - Operations Booklet
FFIEC IT Examination Handbook - Business Continuity Booklet
OSFI B-13 Technology and Cyber Risk Management
Interagency Guidance on Third-Party Relationships (Board, FDIC, & OCC) 06.2023
Learn about the regulations, standards, guidelines, and laws, that our assessments map to here >
Free Sample
System and Organization Controls (SOC) Assessment
Get a sample copy of this risk assessment to see how Venminder can reduce your work and help you identify potential gaps at your vendor before they disrupt your business or your customers.
Free Resources
Ensure Your Third Parties can continue to Support you when faced with the Unexpected
Explore Venminder

Managed Services

Continuous Monitoring

Software Platform

Why Choose Venminder

Continue your Education


























