VENDILIGENCE™
Data Protection Assessment
Our Data Protection Assessment (DPA) is a comprehensive risk-based review of the controls your vendor or suppliers have in place to protect against cybersecurity threats and meet data privacy regulations. The assessment is aligned with global industry guidelines, frameworks, standards and laws.

PRODUCT TOUR
See it in Action: Take a tour of the Data Protection Assessment
See the valuable insights you could gain to streamline and make better risk-based decisions when evaluating your vendor or supplier's data protection practices.
Most Commonly Used For:
Critical and Medium/High Risk Technology Third Parties
We assess the key domains covering
supplier and vendor data privacy practices
-
Data Privacy
-
Security Testing
-
Information Security Governance
-
Sensitive Data Security
-
Resiliency
-
Business Continuity
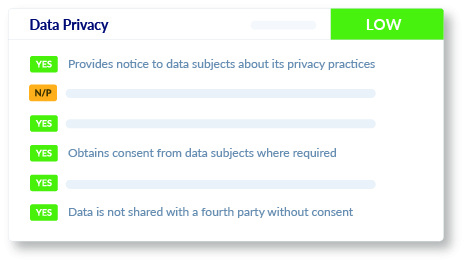
Data Privacy
We conduct an in-depth review of your vendor or supplier's data privacy practices, covering breach notifications, privacy notices, data requests, consent, and sharing with fourth parties, ensuring alignment with industry guidelines, frameworks, standards and laws.
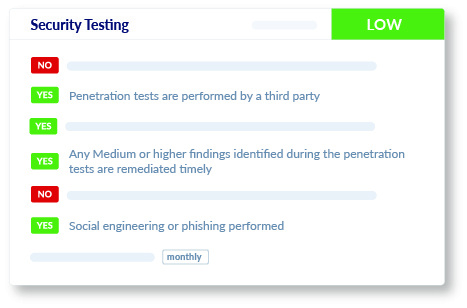
Security Testing
We administer a review to provide you with insights into your vendor or supplier’s penetration testing, vulnerability scanning, and social engineering exercises carried out on their systems and personnel.

Information Security Governance
Our assessment on information security governance provides a clear view of whether the vendor or supplier has formal programs, policies and industry standard practices in place, such as whether they have an information security policy, have a designated CISO, conduct background checks and more.
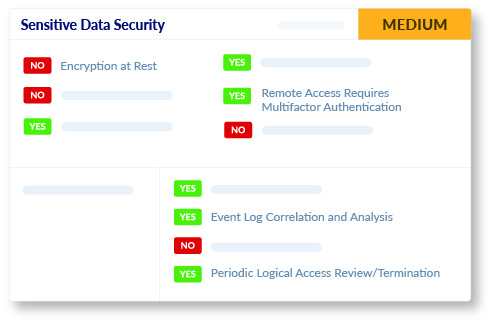
Sensitive Data Security
We evaluate the security practices employed by your vendors or suppliers to protect sensitive data that is stored and processed. Our assessment covers encryption, secure device configuration, incident detection and response, as well as their application security.
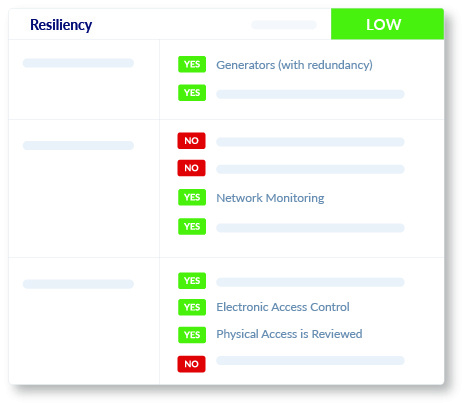
Resiliency
We assess the ability of your vendor or supplier to withstand virtual and physical potentially business-impacting events, including reviewing controls ranging from data backups to on-site generators to better understand the potential for uninterrupted continuation of your business operations, even in challenging situations.
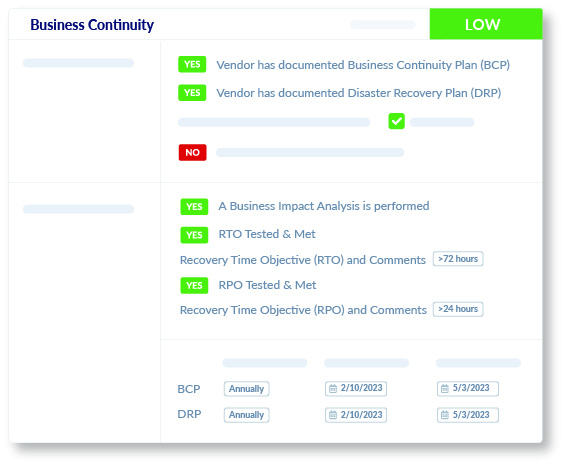
Business Continuity
We determine your vendor or supplier's capacity to provide services during unexpected business disruptions, and their ability to resume normal operations, including Recovery Time Objective and Recovery Point Objective. We also verify that they have documented business continuity and disaster recovery plans in place.
Augment your team and streamline supplier and vendor data protection reviews
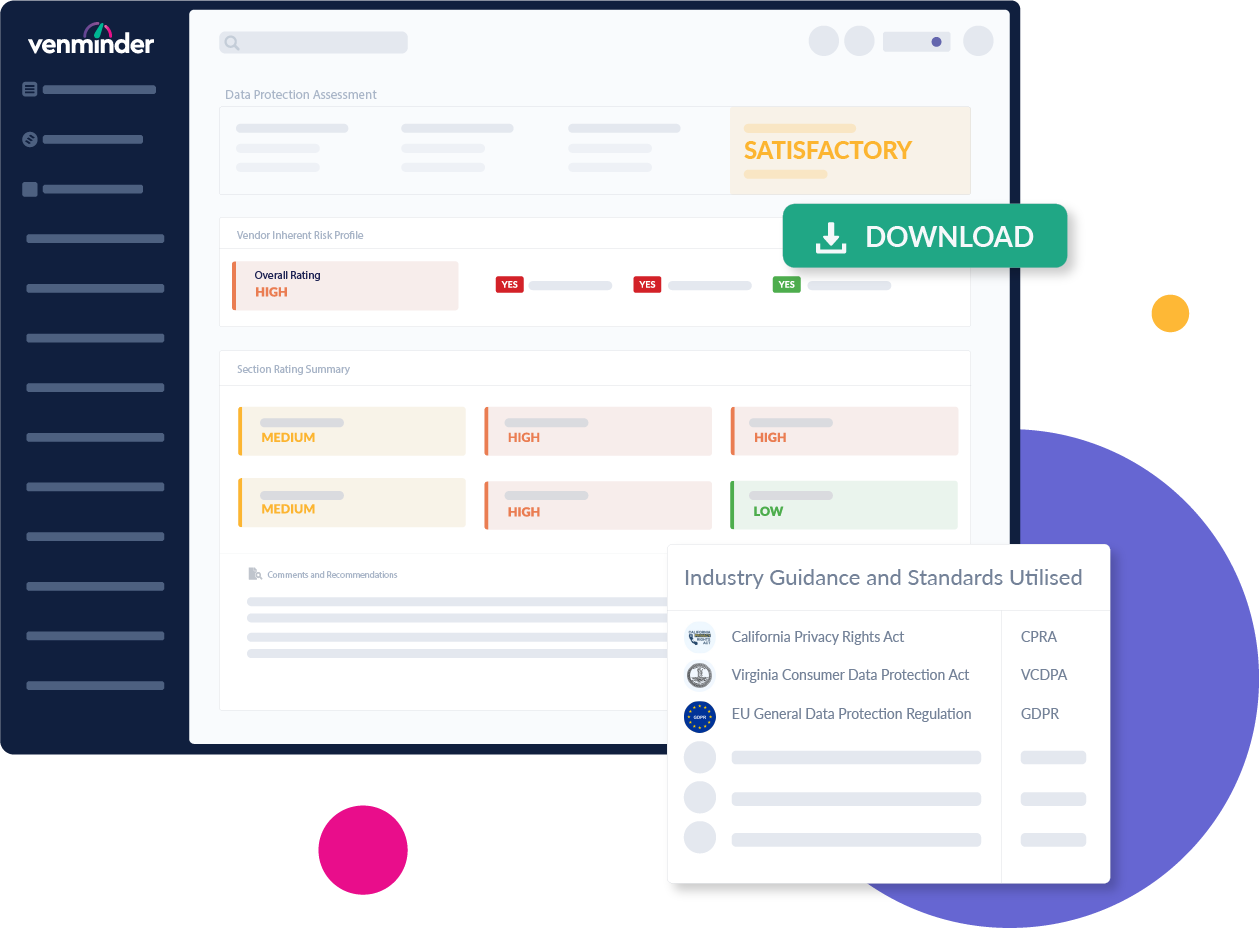
Expert Risk Ratings
At a glance, you'll know if there are any key risks posed to your organization's operations, assets and customers relating to information security governance, security testing, sensitive data security, business continuity, resiliency and data privacy.
Regulation-Specific Insights
Get insights aligned to important data protection regulations like GDPR, VCDPA, CPRA, to determine if your vendor has you in or out of compliance with data privacy laws.
Ensure vendor and supplier compliance with data privacy laws and regulations
Navigating the intricate landscape of local, national, and international data protection laws and regulations can be daunting. Keeping pace with the evolving regulations requires constant vigilance and deep expertise. Data privacy compliance responsibility extends throughout the supply chain where your organization could face severe consequences for failures by a vendor.
We thoroughly evaluate your vendor's data protection practices for alignment with regulations and standards, ensuring the vendor has implemented critical controls found within regulatory requirements, standards, frameworks, and laws, including US state and international privacy laws, such as CPRA, VCDPA and GDPR. This assessment enables your organization's decision-makers to quickly assess, spot areas of concern and give the information needed to address the data risks associated with vendors confidently.
Expertise you can trust
Assessing a vendor's data protection controls involves collecting and reviewing numerous documents. This process demands the knowledge and skills of professionals in information security and often exceeds your internal resources' available time or capabilities.
Our experienced data protection professionals handle the evidence collection and review your vendor's data protection controls to provide a comprehensive risk-based assessment. This approach allows your team to skip the tedious work and can focus on the finished assessment to understand the risks associated with your vendor. Our team stays up-to-date and continuously keeps our Data Protection Assessment aligned with the latest data protection practices and regulations.
Build a consistent evaluation framework for assessing your vendors and suppliers
Creating a consistent approach to assessing your technology vendor data practices is time-consuming, requires defining clear specifications and indicators, risk ratings and keeping that approach current with new standards.
Our assessment offers a standardized and reliable way to compare and evaluate your vendor's data protection controls. This consistency ensures that each assessment meets the highest quality standards and covers the latest key controls. You can use the assessment to quickly drill down to the topics or specific items you are most concerned with, identify action items and priorities for follow-up due diligence based on risk-ratings and data insights.
How it works
STEP 1
Collection of evidence and documents
Venminder’s team directly works with your vendor or supplier to collect the numerous technical documents needed for a qualified and comprehensive assessment of data practices.
STEP 2
Review by information security professionals
Venminder’s experienced information security professionals thoroughly examine the evidence to assess whether your vendor or supplier has implemented critical data protection controls.

STEP 3
Streamlined assessment delivery
You receive an easy-to-understand risk assessment on your vendor or supplier's data protection controls that is available on the Venminder platform and as a downloadable PDF, our reports are easy to understand and are perfect for internal sharing, review, and decision-making.
STEP 4
Better risk-based decisions that protects data
You and your organization’s decision-makers can now make an informed choice about data privacy risks posed by the vendor or supplier and take action to mitigate or address them with confidence.

Discover why Venminder
is top-rated by customers
Ensure vendor and supplier compliance with industry guidelines, frameworks, standards and laws
Technology Standards and Frameworks
AICPA Trust Services Criteria
ISO/IEC 27001:2022
NIST Framework for Improving Critical Infrastructure Cybersecurity version 1.1
NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations
NIST SP 800-63b Digital Identity Guidelines
Regulations, Statutes, and Laws
California Consumer Privacy Act
California Privacy Rights Act
Canadian Personal Information Protection and Electronic Documents Act
China Personal Information Protection Law
Colorado Privacy Act
Connecticut Data Privacy Act
EU General Data Protection Regulation
Health Insurance Portability and Accountability Act
Interagency Guidelines Establishing Information Security Standards
Interagency Guidance on Third-Party Relationships
New York Department of Financial Services - 23 NYCRR 500
Industry Guidance
Center for Internet Security – Critical Security Controls v8
FFIEC IT Examination Handbook – Audit Booklet
FFIEC IT Examination Handbook – Business Continuity Booklet
FFIEC IT Examination Handbook – Management Booklet
FFIEC IT Examination Handbook – Operations Booklet
FFIEC IT Examination Handbook – Outsourcing Technology Services
FFIEC IT Examination Handbook - Wholesale Payment Systems Booklet
FINRA Report on Cybersecurity Practices
OCC 2021-36 Authentication and Access to Financial Institution Services and Systems
SEC Regulation SCI reference to NIST 800-53 Rev. 4
Learn about regulations, standards and guidelines to which the DPA maps here >
Free Sample
Data Protection Assessment
Get a sample copy of this data protection risk-based assessment to see how Venminder can help you identify areas of possible weakness in your vendor or supplier's data protection practices.
Free Resources
Data Protection when Outsourcing to Vendors and Suppliers

Managed Services

Continuous Monitoring

Software Platform

Why Choose Venminder

Continue your Education