How to Successfully Navigate Vendor Risks in Higher Education
By: Venminder Experts on August 14 2024
6 min read

Like many other industries facing significant economic challenges, colleges and universities have turned to third-party vendors to manage overall operating expenses and reduce overheads. These vendors often perform critical operations and provide key services for students, faculty, and staff. However, they can also create additional financial burdens and strain a higher education institution’s resources.
For instance, a university that suffers a third-party data breach could face added expenses through legal fees, regulatory fines, and increased insurance premiums. Recovering from a data breach can also require a significant investment of time and resources through investigative work, security testing, and notifying students and faculty of a breach.
A vendor’s full value can only be realized if its inherent risks, such as cybersecurity, financial, and operational, are managed through the practice known as vendor risk management (VRM). Let’s take a look at some of the other ways unmanaged vendor risk can impact a higher education institution. You’ll also learn how the vendor risk management lifecycle can mitigate these risks and help protect your institution’s resources.
The Impact of Vendor Risks in Higher Education
After several high-profile cyberattacks through the years, like the MOVEit breach in 2023, it’s common for colleges and universities to focus on the financial costs of cybersecurity incidents. However, it’s also important to consider other ways that vendor risk can negatively impact a higher ed institution’s resources.
Here are a few examples:
- Operational disruptions – A service outage from a technology vendor, like an online learning platform, payroll processer, or library management system, would create significant operational disruptions at a higher education institution. These disruptions can require a lot of time to resolve and redirect IT staff from other priorities. It can also delay or even halt student learning and classes.
- Decreased productivity – Faculty and staff often rely on technology vendors to create more efficiencies, such as automating tasks and tracking important data in a student management platform. Technology vendors that are performing poorly and don’t meet their contractual service level agreements (SLAs) can decrease productivity and require a shift to manual processes.
- Reputational damage – Many vendors in higher education are procured for student needs, such as housing, food services and supplies, online learning, and health services. These vendors are representative of the college or university and can cause significant reputational damage by providing poor quality service or maintaining unethical business practices. Rebuilding a damaged reputation and attracting prospective students requires additional time and resources that may not always be available.
- Noncompliance – Vendors that have access to sensitive data can create compliance issues for a higher education institution by violating privacy laws and regulations. Noncompliance can also be an issue if a vendor’s business practices don’t align with an institution’s internal policies, mission, or values.
For example, a university’s commitment to sustainability could be at risk if a vendor doesn’t have a policy in place to address similar issues. Resolving compliance issues and sourcing new vendors can mean that other projects related to innovation and research can’t be prioritized.

Using the Vendor Risk Management Lifecycle in Higher Education
The vendor risk management lifecycle is designed to identify, assess, and manage inherent vendor risks that can cause the negative impacts mentioned above. This is achieved through various activities across three stages – onboarding, ongoing, and offboarding. By using the lifecycle, higher education institutions can adopt a strategy to manage vendor risks effectively. 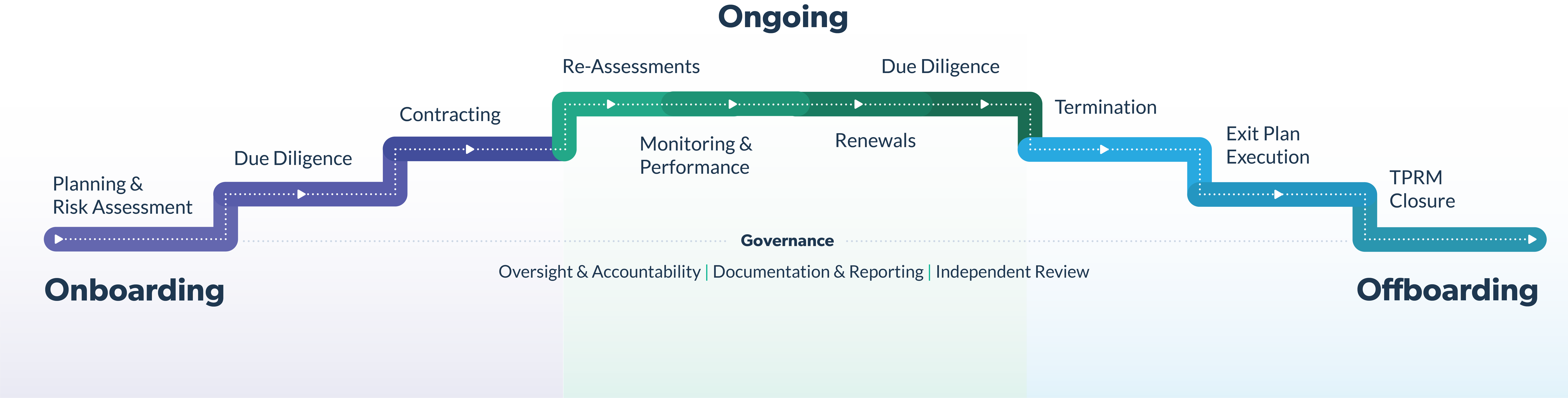
Here’s a closer look at each stage and examples of how their activities mitigate vendor risk at higher education institutions:
- Onboarding involves planning & risk assessments, due diligence, and contracting:
- Planning & risk assessments – One of the first steps in planning the vendor relationship is to determine how you’ll exit the relationship, which can prevent a lot of unexpected costs and resources further down the line. An exit strategy might be switching to another vendor, bringing the product or service in-house, or discontinuing the activity altogether. In addition to planning, it’s important to establish a risk assessment process. To help higher education institutions assess vendor security risks, the Higher Education Information Security Council (HEISC) developed a Higher Education Community Vendor Assessment Toolkit (HECVAT). This is a questionnaire framework specifically designed for higher education institutions to measure information security risks for vendors who access, process, transmit, or store data. However, institutions should consider using this alongside other tools, such as the Standard Information Gathering (SIG) questionnaire, to identify all other inherent risks in a product or service. Risk assessments should determine two elements – whether the vendor is critical to your operations, and the overall risk rating, which is often measured on a scale of low, moderate, or high.
- Due diligence – This process involves collecting and validating vendor information such as SOC reports, business continuity and disaster recovery plans, and financial statements. Due diligence helps ensure controls are in place to mitigate vendor risks that can create negative impacts like operational disruptions and noncompliance.
- Contracting – Negotiating and signing the vendor contract is a significant onboarding activity that will protect a higher education institution from vendor risk. Vendor contracts may include provisions around data security, SLAs, and more, which will ensure the vendor understands the institution’s expectations around performance standards, service quality, and required security practices.
- Ongoing includes risk re-assessments, risk monitoring and performance management, contract renewals, and periodic due diligence:
- Risk re-assessments – A vendor’s risk can change for various reasons, such as the decision to procure a new product or service, an update to the vendor’s processes, or a recent security incident. It’s essential to perform regular risk re-assessments to validate that nothing has changed in the vendor relationship. Critical and high-risk vendors should be re-assessed annually, and moderate-risk vendors can be re-assessed every 18 months to two years. Low-risk vendors can be re-assessed every two to three years or upon contract renewal.
- Risk monitoring and performance management – These activities help ensure the vendor’s risk level and performance remain consistent throughout the contract term. Ongoing monitoring will keep a higher education institution informed of any changes that occur in between formal risk re-assessments, such as declining performance or a new cybersecurity threat that can impact your vendor.
- Contract renewals – Planning your contract renewal in advance can help avoid unexpected costs associated with automatic renewals and price increases. Whether your institution decides to negotiate for better terms, or begin looking for an alternative vendor, it’s important to establish a contract management strategy that includes sufficient time for the renewal period.
- Periodic due diligence – In addition to risk re-assessments, it’s important to perform periodic due diligence throughout the vendor relationship. This means reviewing the vendor’s information on file to make sure you have the most current documents. Business continuity plans, insurance certificates, and SOC reports aren’t valid indefinitely and should be collected before they expire.
- Offboarding will involve termination, exit plan execution, and third-party risk management (TPRM) closure:
- Termination – Implementing a termination process that includes formally notifying your vendor and following the contract terms can help keep a higher education institution aware of fees or penalties they may be subject to pay.
- Exit plan execution – The established exit strategy is executed through a step-by-step exit plan, which outlines both parties’ responsibilities for ending the relationship. An exit plan should also contain contingency plans if the vendor fails to meet their obligations, which can create additional costs for your institution.
- TPRM closure – Formally closing the vendor relationship within your internal systems, such as accounts payable, contract management, and procurement, will help ensure final invoices are paid, and automatic payments are suspended.
By implementing and maintaining these comprehensive vendor risk management practices, higher education institutions can identify, assess, and manage vendor risks more effectively, which ultimately delivers more value from outsourcing. Colleges and universities are now outsourcing many of the functions previously considered core to their mission. Despite the importance of cybersecurity as a cornerstone of vendor risk management, institutions should also consider a robust vendor risk management program designed to identify and manage vendor risk in all its forms.
Infographic
Donec nec justo eget felis facilisis fermentum. Aliquam porttitor mauris sit amet orci.

Related Posts
Minimizing the Risk of IoMT Device Vendors in Healthcare
The Internet of Medical Things (IoMT) is transforming healthcare. More and more people use these...
TPRM and the Safeguards Rule: How Your Organization Can Comply
As part of the Federal Trade Commission’s (FTC) recently updated Safeguards Rule, financial...
Mortgage Company Vendor Risk Management Software
Over the past few decades, vendor risk management, also known as third-party risk management, has...
Subscribe to Venminder
Get expert insights straight to your inbox.
Ready to Get Started?
Schedule a personalized solution demonstration to see if Venminder is a fit for you.





.gif?width=1920&name=Sample-Graphic-Animation%20(1).gif)


