The FTC Safeguards Rule, Higher Education, and Third-Party Risk Management
By: Hilary Jewhurst on February 28 2023
8 min read

Protecting customer information and privacy is not only a best practice for postsecondary institutions, but, for many, it’s also a regulatory requirement. Student financial aid information obtained for financial aid programs (Title IV) is subject to the FTC's (Federal Trade Commission) Safeguard Rule.
But what exactly is the Safeguards Rule, and what are its requirements? What do Title IV institutions need to do to ensure regulatory compliance? How does the rule apply to your institution's vendors and third parties? To learn more, read on.
What Is the FTC Safeguards Rule?
The Safeguards Rule is also referred to as the Protect Customer Information Rule, and as the name implies, the purpose of the Rule is to protect customer information. Previously, the Safeguards Rule established cybersecurity standards for covered financial entities to maintain and protect customer information. This includes all higher education institutions participating in federal student financial aid programs authorized under Title IV of the Higher Education Act of 1965. Gramm-Leach-Bliley Act (GLBA) cybersecurity requirements must be met by all Title IV institutions, whether public, private, nonprofit, or for profit.
Under the Gramm-Leach-Bliley Act (the Safeguards Rule), the Federal Trade Commission (FTC) published a final rule amending the requirements for safeguarding customer information on December 9, 2021. Amendments to the Rule are reflective of today's risk landscape and technology.
Compliance with the amended rule is required by June 2023.
Requirements of the Safeguards Rule
- A Qualified Individual must implement and supervise your institution's information security program. Individuals qualified for this position can be employed by your institution, an affiliate, or a service provider. This individual must have the requisite skills and experience to build and implement your information security program and should be supervised by a senior-level employee. Remember, even if you choose to outsource this position, your institution is still responsible and accountable for information security risks.
- You must conduct a risk assessment of your data and information environment. Effective security begins with understanding your institution's information ecosystem. You must know what data you have and where and how it is accessed, transmitted, processed, or stored. Once you have identified the data, you should determine what foreseeable risks or threats will likely threaten its security, confidentiality, or integrity, both internally and externally. Your institution must address how customer information could be disclosed, misused, altered, or destroyed without authorization. Your risk assessment must be documented and clearly identify the criteria for measuring and evaluating information security risks.
- The institution must create and implement safeguards to mitigate the risks. Under the Safeguards Rule, your institution must do the following (among other things):
- Know what you have and where you have it. Conduct a periodic data inventory, noting where it's collected, stored, or transmitted. Keep an accurate list of all systems, devices, platforms, and personnel.
- Implement and periodically review access controls. Determine who has access to customer information and regularly reconsider whether they still have a legitimate business need
- Maintain a log of authorized users' activity and monitor for unauthorized access. Implement procedures and controls to monitor when authorized users access customer information on your system and detect unauthorized access.
- Implement multi-factor authentication for anyone accessing customer information on your system. For multi-factor authentication, the Rule requires at least two of these authentication factors:
- A knowledge factor (for example, a password)
- A possession factor (for example, a token)
- And an inherence factor (for example, biometric characteristics)
- Encrypt customer information on your system and when it's in transit. When encryption is not feasible, use effective alternative controls approved by the Qualified Individual supervising your information security program.
- Risk assess your apps. Your institution should implement procedures for evaluating the security of any apps it develops or uses to store, access, or transmit customer information.
- Anticipate and evaluate changes to your information system or network. Information security programs must include change management as part of the Safeguards Rule.
- Dispose of customer information securely. Ensure that your customer information has been securely disposed of no later than two years after you last used it to serve the customer. There are two exceptions to this rule:
- There is a legitimate business need or legal requirement to retain the information
- Due to the way information is maintained, targeted disposal is not possible.
- Maintain regular monitoring and testing of your safeguards. Make sure your procedures are effective at detecting attempted and actual attacks. Continuously monitor your information systems.

- Staff training must be provided regularly. Employees and staff must be provided with security awareness training and schedule regular refreshers. Insist on specialized training for employees, affiliates, or service providers responsible for implementing your information security program
- Keeping the information security program current. Your program must remain flexible to address changes in your operations and personnel or due to risks identified through assessments or emerging threats.
- Developing a documented incident response and plan. Every institution needs a response and recovery plan in case of a security event – or an episode resulting in unauthorized access to or misuse of information stored on your system or maintained in physical form. The Safeguards Rule requires that the plan must cover:
- The goals of your plan
- The institution's internal response to a security event
- Clear roles, responsibilities, and levels of decision-making authority
- Communications and information sharing both inside and outside your institution
- A method for fixing any weaknesses found in your control and system architecture
- Procedures for documenting and reporting security events and your institution's response; and
- Post-mortem analysis and revisions to your incident response plan and security program based on your findings
- Requiring your Qualified Individual to report to your board of directors. Your Qualified Individual must report in writing regularly – and at least annually – to your board of directors or governing body. The report should include:
- The overall assessment of your institution's compliance with its information security program
- Risk assessment, risk management, and control decisions
- Service provider arrangements
- Test results
- Security events and how management responded
- Recommendations for changes in the information security program
- Monitoring your service providers. The Safeguards Rule requires the institution to select service providers (also known as vendors and third parties) with the skills and experience to maintain appropriate information security safeguards. Although the concept of monitoring your service providers is fairly straightforward, the execution of this specific requirement is fairly complex and entails vendor-specific risk assessments, evaluation of their controls through comprehensive due diligence, carefully written contracts, periodic re-assessment, performance management, monitoring, and more.
How Can Third-Party Risk Management Help Postsecondary Educational Institutions Protect Customer Data?
Implementing a third-party risk management program is the best way to select, evaluate, manage, and monitor your service providers.
A formal third-party risk management program provides the framework to identify, assess, manage, and monitor risks presented to the institution and its customers through third-party relationships. While these processes help to protect institutional and customer data, third-party risks aren't limited to just information security and privacy risks. All third-party relationships carry at least some risk, and each product or service has different types and amounts of risks associated with it, including:
- Operational risk
- Business continuity risk
- Financial risk
- Legal and compliance risk
- Reputational risk
- Transactional risk
As the Safeguards Rule outlines, service providers are expected to be supervised. Postsecondary educational institutions can easily meet these requirements with the right third-party risk management practices and vendor risk management lifecycle.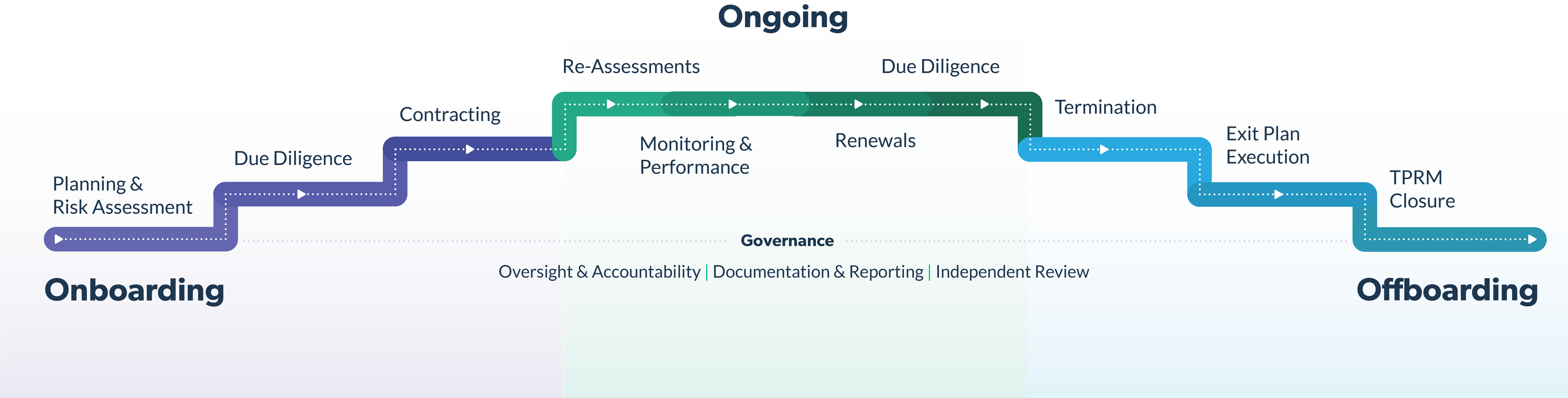
The Safeguards Rule requirements can be addressed through third-party risk management and adherence to the vendor risk management lifecycle.
| Safeguards Rule Requirement | Third-Party Risk Management Lifecycle Activities |
Lifecycle Stage |
|
Taking reasonable steps to select and retain service providers that are capable of maintaining appropriate safeguards for customer information |
|
Onboarding |
| Requiring your service providers by contract to implement and maintain such safeguards |
|
Onboarding |
| Periodically assess your service providers based on the risk they present and the continued adequacy of their safeguards |
|
Ongoing Monitoring |
Benefits of Third-Party Risk Management
There are many benefits of third-party risk management, such as:- A scalable and repeatable third-party risk management program will help your organization comply with the Safeguards Rule.
- The risk of every partner and vendor can be identified, assessed, and managed by your institution through formalized and repeatable risk management processes.
- Using standardized risk questionnaires, you can identify what consumer data the vendor accesses, processes, transmits, or stores. An effective due diligence process can identify whether the vendor has adequate controls to manage these risks.
- After analyzing the control environment, your institution can ensure that the contract includes required information security safeguards by documenting information security safeguards as a contractual requirement.
- The institution should monitor risks constantly and re-assess vendor risks periodically to ensure that any new risks are identified.
Recent amendments to the FTC's Safeguards Rule impose strict protections for customer data on covered financial institutions (including Title IV educational institutions). Institutions must have specific internal safeguards and identify and assess the risks associated with their service providers and vendors.
Identifying, assessing, and managing these risks might be challenging for institutions without a formal third-party or vendor risk management program. Still, compliance with the Safeguards Rule isn't optional. Third-party risk management is the perfect tool for institutions to identify and mitigate third-party risks, whether for complying with the Safeguards Rule or trying to identify and mitigate third-party risks. So there is no better time to get started with third-party risk management.
toolkit
Ensure you're following the steps of the third-party risk management lifecycle to maximize the benefits of your program.

Related Posts
TPRM and the Safeguards Rule: How Your Organization Can Comply
As part of the Federal Trade Commission’s (FTC) recently updated Safeguards Rule, financial...
Safeguards Rule Requires Auto Dealerships to Do Third-Party Risk Management
Originally published August 18, 2022 but has now been updated to reflect regulatory changes. Under...
Cloud Service Provider Breach: Lessons From the Snowflake Attack
If your organization relies on a cloud service provider (CSP), the recent Snowflake data breach has...
Subscribe to Venminder
Get expert insights straight to your inbox.
Ready to Get Started?
Schedule a personalized solution demonstration to see if Venminder is a fit for you.
